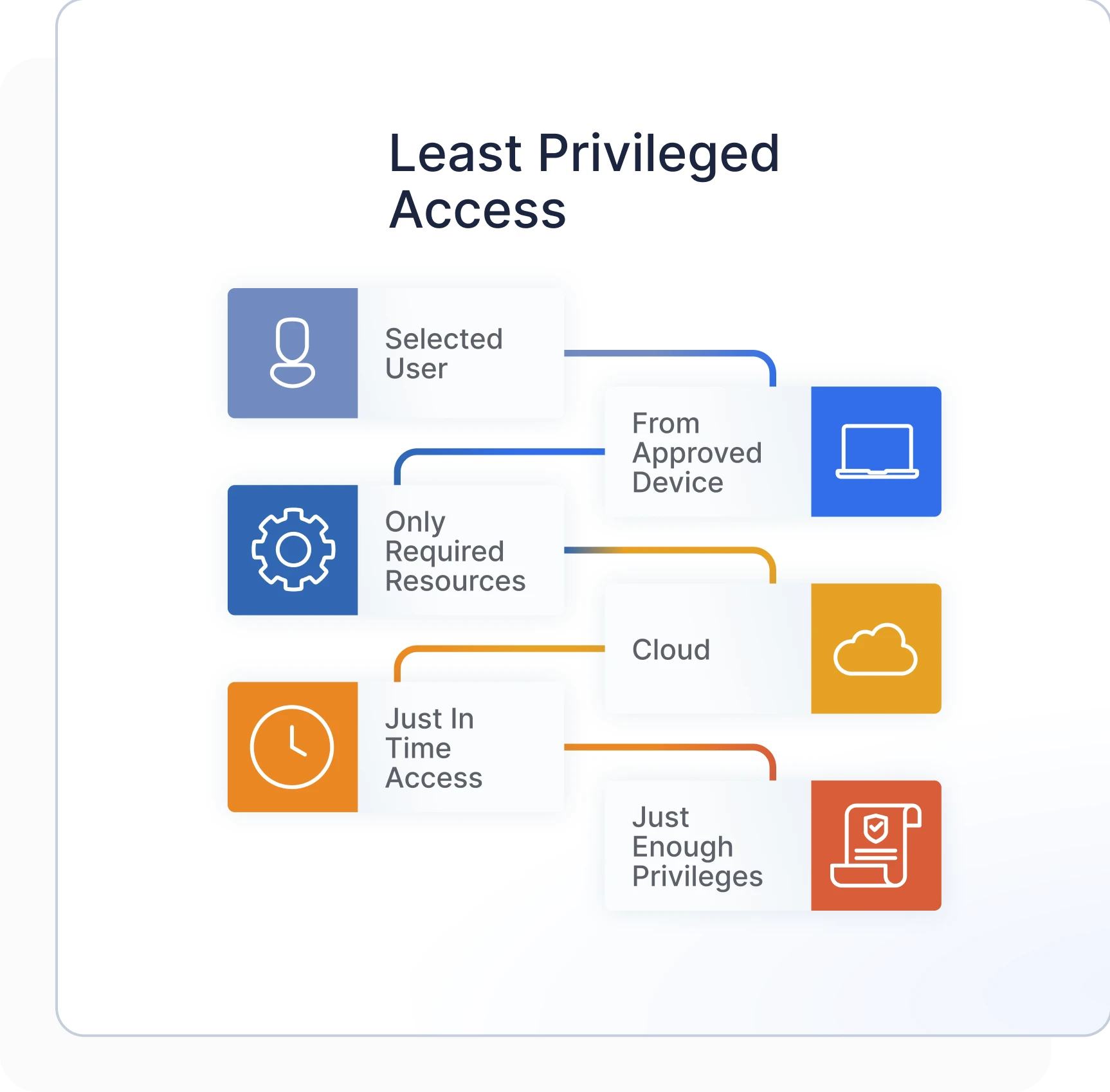
Privileged Access Management
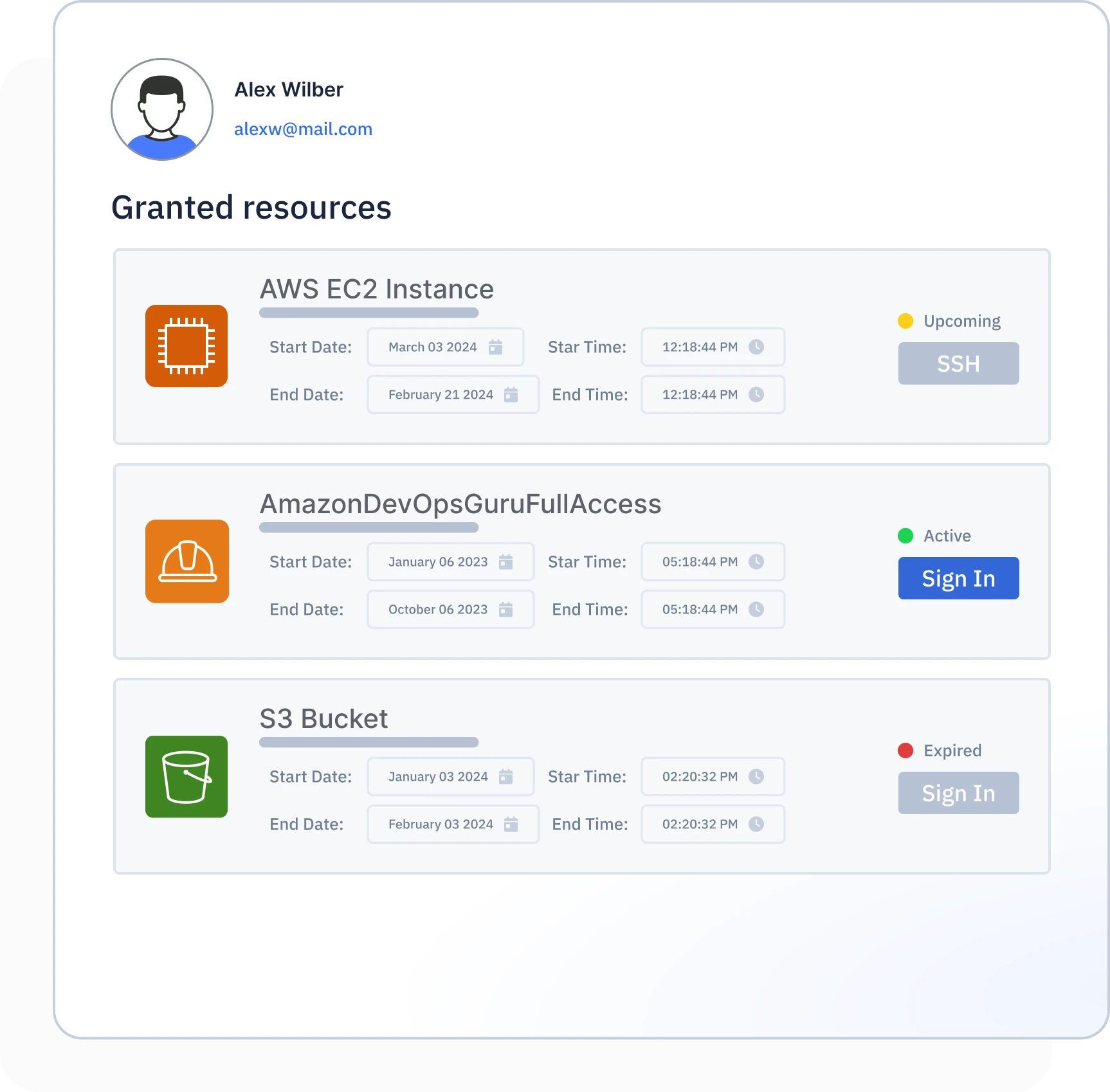
Self Service Portal
Minimize your organization’s attack surface and secure your sensitive data by limiting who gets access and when. Turn on Just-In-Time access to significantly reduce your organization’s attack surface using simplified approval system.
Passwordless
Cloud Infrastructure
Scale faster and stop credential sprawl by eliminating shared accounts and static credentials that are challenging to track. Developers can access resources in AWS, GCP, and Azure using native tools without using any form of static credentials.

Compliance
Get complete visibility into every deployed resource, every user access, and the policies that define and govern access in today’s dynamic multi-cloud landscape. Get information at your fingertips: who accessed what, when, how long, which device, and which permission.
Cloud
Identity Governance
Protect your organization’s cloud infrastructure by automating risk analysis for all permissions granted to all resources across multi-cloud. Build least privilege access to all users using flexible controls to right-size the permissions.
Get in touch
Want to know more about our product? Please fill out the form and share your message with us.
- Request a demo
- Business tiers and pricing
- General questions