Glossary
Single Sign-On vs. Multi-Factor Authentication: Understanding the Differences
Learn the key differences between Single Sign-On (SSO) and Multi-Factor Authentication (MFA) in this comprehensive guide.
Table of Content
Every organization is concerned about protecting their users’ identities and sensitive information. Two of the top technologies that address these needs are Single Sign-On (SSO) and Multi-Factor Authentication (MFA). Both are critical in protecting digital identities but cover different security requirements. To be able to make an informed decision regarding which solution best works for your organization, you need to know what each technology stands for and how they can complement each other.
What is Single Sign On?
Imagine the nightmare of having to remember a unique password each time you log in to an online service! This would result in you reusing passwords multiple times for different services, creating an easy entry for any bad actor. SSO is the solution to this problem. It unifies the authentication process, enabling you to access a range of online services and applications with just one set of credentials.
The core concept in SSO is the Identity Provider (IdP), which acts as a central authority that verifies the identity of users. Thus, every time a user logs into any Service Provider, they will be redirected to an IdP for authentication. It grants access on verification to the service requested, and thus removes the repetitive task of logging into every website.
Apart from being extremely convenient, it provides stronger security by discouraging weak or reused passwords.
How does SSO Work?
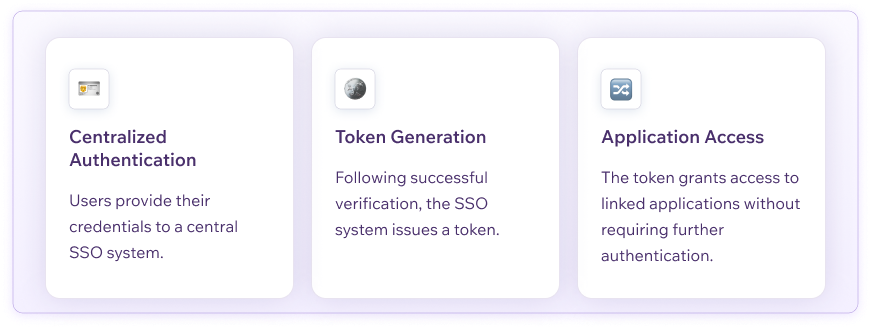
Centralized Authentication. Users provide their credentials to a central SSO system.
Toke Generation: Following successful verification, the SSO system issues a token.
Application Access:, The token grants access to linked applications without requiring further authentication.
Benefits of SSO
The benefits of SSO include:
Enhanced Security: Because SSO reduces the count of logins, there are fewer attempts at login and therefore less vulnerability to attacks. Other benefits include the encouraging use of complex passwords, since users will be less inclined to use easy ones over and over again. Additionally, SSO works well with multi-factor authentication to add another layer of security.
Improved User Experience: SSO significantly enhances user experience by streamlining access to multiple applications with a single login. This eliminates the frustration of managing numerous passwords and saves valuable time, boosting productivity. The consistent login process across different systems creates a seamless and user-friendly experience.
Cost Savings: By reducing the frequency of password-related issues, SSO helps organizations minimize IT support costs. Furthermore, automating user account management through SSO streamlines administrative tasks, leading to overall cost savings.
Compliance Benefits: It aids organizations in adhering to data privacy regulations by centralizing user management and control. Comprehensive audit trails generated by SSO systems facilitate compliance efforts and accountability.
Additional Benefits: Its adaptability extends to risk-based authentication (RBA), allowing for dynamic security measures based on user behavior and context. This additional security layer effectively protects sensitive information. Moreover, SSO can be implemented in customer-facing applications, providing a smoother experience for external users and strengthening customer relationships.
What is Multi-Factor Authentication?
While SSO streamlines the login process, it’s essential to recognize its limitations. A compromised password can grant an attacker access to multiple accounts. This is where MFA steps in. By demanding multiple forms of verification, MFA significantly elevates security.
MFA requires users to provide proof of identity by presenting knowledge (password, PIN), possession (security token, smartphone), or inherent traits (fingerprint, facial recognition). Combining two or more of these factors creates a formidable barrier against unauthorized access.
For instance, when you log in to your corporate slack account, you’ll typically need to provide a password and then verify your identity using a one-time code sent to an authenticator app on your mobile device. This layered approach significantly enhances security by reducing the risk of account takeover, even if a hacker has stolen your password.
How Does MFA Work?
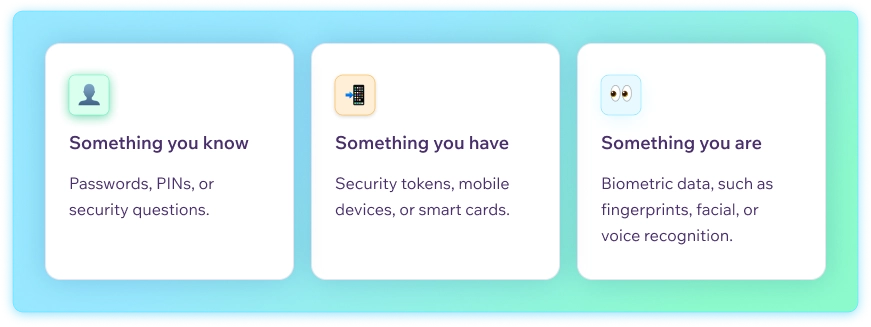
Something you know: Passwords, PINs, or security questions.
Something you have: Security tokens, mobile devices, or smart cards.
Something you are: Biometric data, such as fingerprints, facial, or voice recognition.
Benefits of MFA
Here are the top reasons why MFA is essential:
1. Enhanced Account Recovery: MFA can expedite the account recovery process without sacrificing security. By requiring multiple forms of identification, MFA enables users to regain access to their accounts while ensuring that only authorized individuals can proceed.
2. Protection Against Credential Stuffing: Credential stuffing, a common attack where hackers use stolen credentials to access multiple accounts, is rendered significantly less effective with MFA. Even if your login information is stolen, this prevents unauthorized access to your accounts.
2. Improved Fraud Detection: By adding an extra layer of authentication, MFA can help detect fraudulent activity. Unusual login attempts or failed MFA attempts can trigger alerts, allowing for timely intervention and prevention of financial loss.
3. Stronger Compliance Posture: Many industries and regulatory bodies mandate the use of MFA to protect sensitive data. Implementing MFA demonstrates a strong commitment to data security and helps organizations meet compliance requirements.
4. Increased User Productivity: While it might seem counterintuitive, MFA can actually increase user productivity. By preventing unauthorized access and reducing the frequency of password resets, MFA can save employees time and frustration, allowing them to focus on their work.
Key Differences Between SSO and MFA
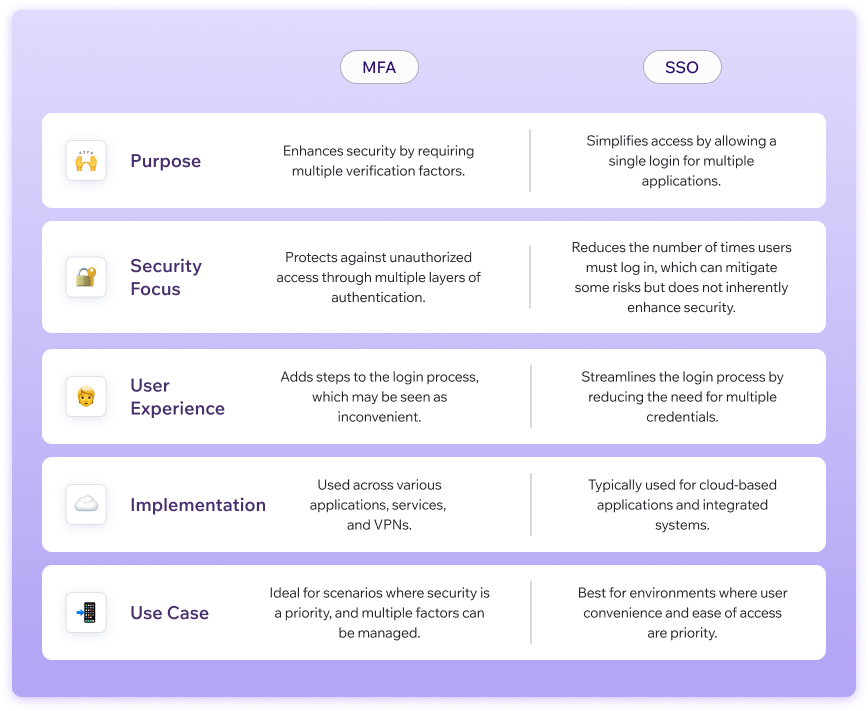
MFA Purpose: Enhance security by requiring multiple verification factors.
SSO Purpose: Simplifies access by allowing a single login for multiple applications.
MFA Security Focus: Protects against unauthorized access through multiple layers of authentication.
SSO Security Focus: Reduces the number of times users must log in, which can mitigate some risks but does not inherently enhance security.
MFA User Experience: Adds steps to the login process, which may be seen as inconvenient
SSO User Experience: Streamlines the login process by reducing the need for multiple credentials.
MFA Implementation: Used across various applications, services, and VPNs.
SSO Implementation: Typically used for cloud-based applications and integrated systems.
MFA Use Case: Ideal for scenarios where security is a priority, and multiple factors can be managed.
SSO Use Case: Best for environments where user convenience and ease of access are priority.
Combining SSO and MFA for Optimal Security
While SSO and MFA have distinct functions, they can work together to create a robust security framework.SSO provides a convenient user experience, while MFA adds an essential layer of protection.
SSO allows users to access multiple applications with one set of credentials, simplifying the login process and improving user experience. However, it relies on the security of those credentials alone. MFA, on the other hand, adds layers of security by requiring additional verification methods—such as a code sent to a phone or biometric scan—beyond just the password. This means that even if credentials are compromised, unauthorized access is less likely. While SSO streamlines access, MFA strengthens it, and using both together provides a robust security framework.
Advanced Strategies for Strengthening SSO and MFA
To maximize the effectiveness of SSO and MFA, organizations should consider the following:
Risk-Based Authentication: Adapting authentication requirements based on factors such as user behavior, location, and device can provide a more granular approach to security.
Passwordless Authentication: Exploring passwordless options like biometrics or security keys can further enhance security and user experience.
User Education: Implementing comprehensive security awareness training is essential to empower users to make informed decisions and protect themselves from cyber threats.
Regular Security Assessments: Conducting periodic security audits and vulnerability assessments helps identify potential weaknesses and improve overall security posture.
Conclusion
Both SSO and MFA are indispensable components of a comprehensive security strategy. SSO optimizes user experience by simplifying the login process, while MFA reinforces security by demanding multiple forms of verification. By understanding their unique roles and implementing them strategically, organizations can establish a secure and efficient digital environment.
It’s crucial to remember that while SSO enhances convenience, it’s not a substitute for robust password hygiene. Users should continue to employ strong, unique passwords and consider additional security measures like password managers.
By effectively integrating SSO and MFA, organizations can strike a balance between usability and security, safeguarding valuable assets while providing a seamless user experience.