Cloud data powerhouse Snowflake is making headlines, but not for reasons they’d prefer. A notorious hacking group, UNC5537, has been targeting Snowflake customer accounts in a daring campaign to steal data and extort ransoms. While Snowflake’s core systems remain secure, about 165 customers had their data compromised through stolen credentials.
The Heist Unveiled: What We Know
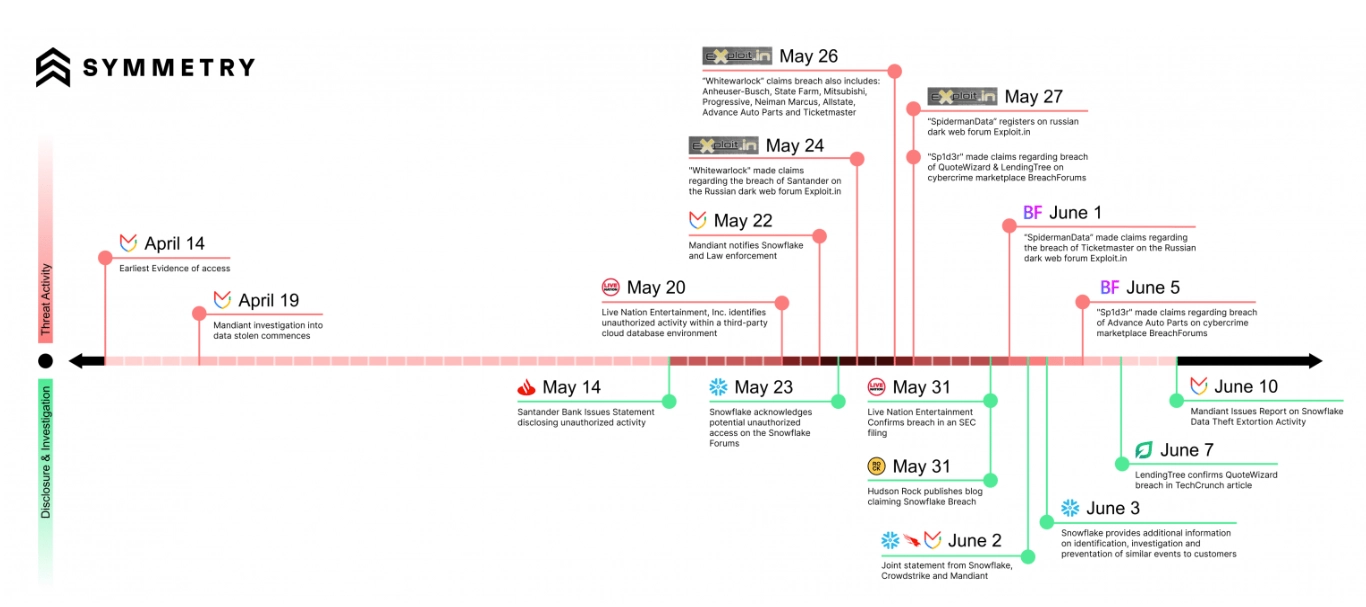
In April 2024, security researchers discovered a concerning trend – a hacking group known as UNC5537 was targeting Snowflake customer accounts. The goal? Data theft and extortion. While initial reports caused a stir, the true extent of the campaign has recently come to light. Over 165 Snowflake customers had their data compromised, not through a vulnerability in Snowflake’s platform itself but through a more insidious method – stolen credentials.
The attackers leveraged infostealer malware, a program that steals login information from unsuspecting users. These stolen credentials, some dating back to 2020, were then used to access customer accounts within Snowflake. Once inside, the attackers used these stolen credentials to access customer accounts and exfiltrate sensitive data. Now, they’re attempting to sell this stolen information on the black market and pressure companies into paying ransoms.
Source: Security Boulevard
The Wake-Up Call: Secure Your Cloud
Despite the breach, Snowflake’s platform remains unscathed. The weak link was the individual customer accounts, compromised through credential theft. Snowflake, alongside Mandiant and CrowdStrike, confirmed in a joint statement that the breach wasn’t due to a flaw in their platform. Instead, the attackers exploited compromised credentials for accounts that lacked multi-factor authentication (MFA).
This incident is a wake-up call for all organizations utilizing cloud-based storage solutions. Security is a shared responsibility, requiring resilient security and compliance practices are essential at both the platform and customer levels.
Power-Up Your Cloud Security With Procyon
While the Snowflake incident raises concerns, it also presents an opportunity to strengthen your cloud security posture. Procyon, a comprehensive On-demand Access Management solution, empowers organizations to take control of their cloud environment and mitigate the risks associated with stolen credentials. Here’s how Procyon’s capabilities can strengthen your defenses:
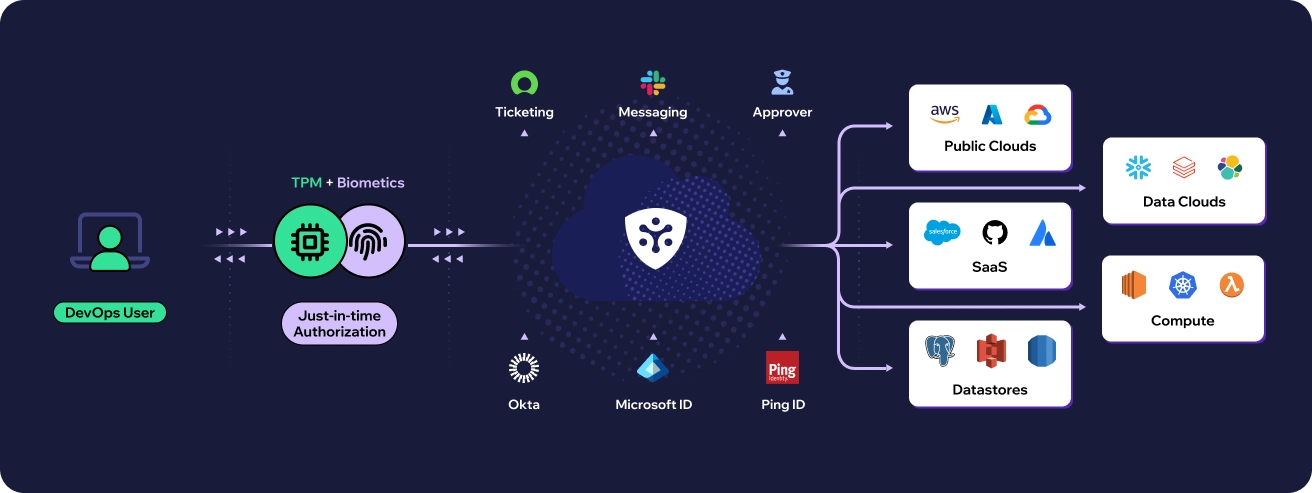
- Multi-Factor Authentication (MFA): Comprehensive Security for Snowflake: Procyon offers end-to-end integration for Snowflake with built-in MFA, ensuring robust protection for all login attempts. Users are required to verify their identity using additional factors beyond passwords, such as one-time passcodes from authentication apps or hardware tokens. This approach not only enhances security by thwarting unauthorized access attempts but also supports passwordless authentication, streamlining user access without compromising security measures. Additionally, Procyon seamlessly co-exists with existing identity providers, allowing organizations to leverage their current infrastructure while enhancing security across their Snowflake environment.
- Enhanced Access Security: Strengthening Control and Protection: Procyon employs robust access controls to prevent unauthorized entry right from the outset. It carefully monitors and manages user access to sensitive data, ensuring permissions are finely tuned according to the principle of least privilege. This approach guarantees that users only have essential access, minimizing potential damage in case of a breach. Additionally, Procyon enhances security with advanced features such as TPM and biometric authentication, eliminating the reliance on vulnerable static credentials, making your data virtually impervious to theft. The system proactively alerts administrators to investigate sudden increases in data access or unusual queries, further fortifying security measures.
- Continuous Session Monitoring: Procyon’s platform does not stop at access control! It excels in continuous session monitoring by employing advanced techniques to scrutinize user activities across diverse cloud environments. Leveraging sophisticated algorithms, it detects deviations from established behavioral patterns in real-time. This proactive capability enables immediate identification of suspicious activities, such as unauthorized access attempts or anomalous data retrieval efforts. By flagging these anomalies, we empower security teams to initiate rapid responses, investigate incidents thoroughly, and mitigate potential threats before they escalate into significant security breaches.
- Detailed Audit Logging: Procyon enhances cloud visibility by providing a detailed audit trail that offers complete observability into security and compliance within your Snowflake environment. This capability empowers you to gain profound insights into all activities occurring in your cloud ecosystem. Easily access vital information such as user access details—who accessed what, when, duration, device used, and permissions granted. This comprehensive oversight enables proactive monitoring, rapid incident response, and effective regulatory compliance, ensuring robust protection of your cloud resources with actionable intelligence readily available.
- Enhanced Third-Party Credential Management: Procyon goes beyond securing user credentials by implementing advanced measures to protect third-party credentials used within Snowflake. It ensures that only essential permissions are granted to third-party applications, thereby limiting potential damage in case of a security breach. Additionally, Procyon facilitates regular review and rotation of these credentials to mitigate risks associated with compromised or outdated access. This proactive approach enhances overall security posture, safeguarding sensitive data and maintaining integrity across your cloud environment.
The Snowflake incident underscores the importance of robust cloud security practices. By leveraging Procyon’s advanced capabilities, organizations can effectively mitigate data breach risks, protect valuable cloud assets, and restore customer trust.
Discover how Procyon can enhance your Snowflake cloud security strategy at https://www.procyon.ai/integrations/snowflake/.