Get frictionless, secure access to cloud infrastructure
Procyon
Self Service Portal
- Eliminate productivity bottlenecks of a centralized administrator
- Configure approval policies based on a variety of factors
- View a catalog of granted and unaccessed resources
Procyon
Passwordless Access
- Leverage TPM to strongly identify users and devices
- Stop credential sprawl by removing the burden of passwords
- Works with AWS, GCP, Azure and other native tools
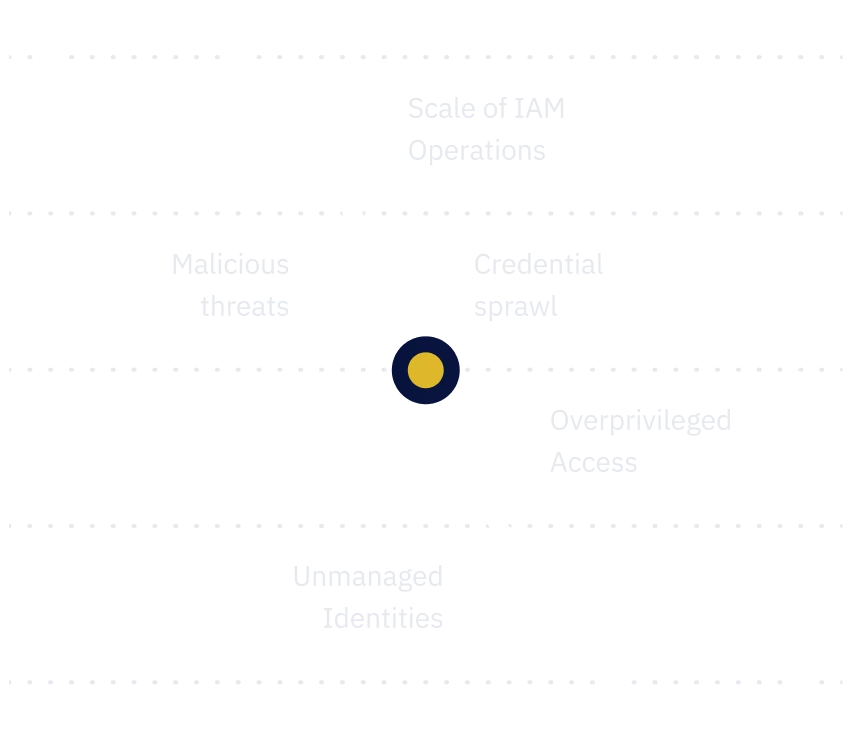
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.
Customer Testimonials
Most relevant product I’ve encountered in the past year. The TPM technology is a clever and effective way of addressing the secrets management problem. It reduces end user/developer friction and is fundamentally more secure rather than exchanging one secret token for another.
The current market solutions and traditional processes for cloud infrastructure access have created a lot of friction for developers and are designed to default to be a road block versus truly authenticating and confidently removing friction.
Recent Resources
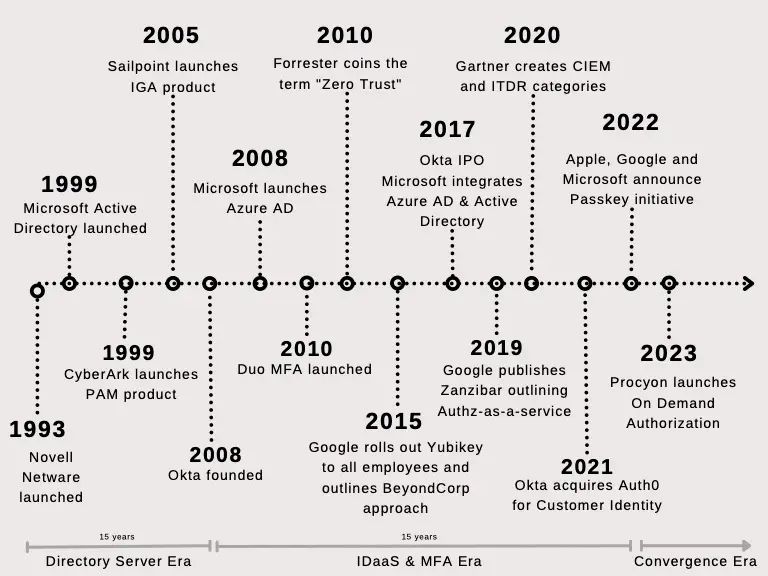
Identity and access management traces its roots back to the mainframe era. DoD first employed logical...
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology....
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now...
Get in touch
Want to know more about our product? Please fill out the form and share your message with us.
- Request a demo
- Business tiers and pricing
- General questions