Browse by Topic
The Sisense Breach: Why Strengthening Credential Security is Priority In today's interconnected digital landscape, cybersecurity breaches have...
Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and discretionary...
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology. Passkey is a friendly brand...
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now famous Turing award acceptance...
Image credit: Unsplash In the previous blog post, we discussed how to protect against the compromise of highly privileged human users. In this post...
Image credit: Unsplash Protecting highly privileged users is at the heart of security 2.0 stack. Easiest way to become the source of a software...
Image credit: Unsplash We are a mid-sized startup and our code base is little over a million lines of code. If we include all the packages we import...
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
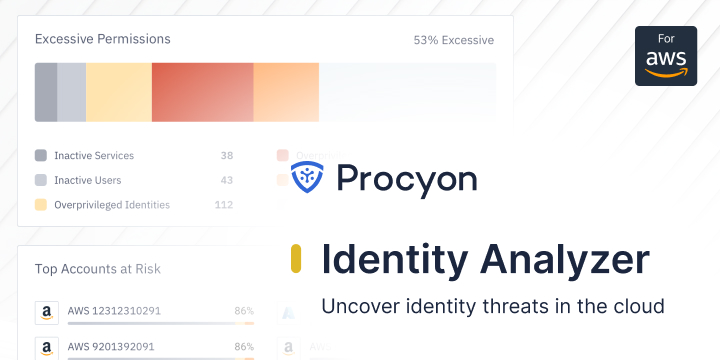
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...