Go Passwordless with Procyon PAM (Privilege Access Management)
Scale faster and stop credential sprawl by eliminating shared accounts and static credentials that are challenging to track.

TPM Security
Procyon leverages a TPM (Trusted Platform Module) chip on modern laptops. The Procyon solution strongly identifies the user and device using the TPM chip, ensuring every transaction is authenticated and authorized continuously.
Stop Data Breaches
Bad actors on the internet don’t break in, they just sign into your accounts. With Procyon, developers and security teams don’t have to worry about credential theft as there are no real credentials stored. Even better, AWS, GCP, Azure CLI, and other cloud native tools work seamlessly.

Passwordless Access for Developers
Passwordless authentication offers users a way to verify themselves without having to remember or manually type passwords. This provides stronger security and fewer breaches. Users can conveniently and securely access applications and services using biometric solutions.
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.

Eliminate the Risk of Standing Privileges with Procyon
Minimize your organization’s attack surface and secure your sensitive data by limiting who gets access and when.
Just In Time Access
Long standing access can be replaced with Just In Time (JIT) access to significantly reduce your organization’s attack surface. JIT is the best way to prevent credential misuse and ensure attackers do not have access to your sensitive data or IT ecosystem.
Self Service Multi-Cloud Experience
Resolve the complexity of permissions across multiple cloud providers with a self service experience. No need to spend time revoking access – it’s all automated. Leverage cloud native APIs for all major cloud providers for a seamless experience right out of the box.


Simplified Approval System
The volume of services, databases and roles in multi-cloud can make privilege and access management challenging. We remove the complexity by generating a one-time token or credential, keeping everything secure and streamlined. Get it done in 3 simple clicks.
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.

Enhanced Protection – Terminate sessions instantly
Terminate sessions immediately if suspicious activity is detected to stop any user, anywhere, anytime.

Stop Malicious Access
Having a kill switch decreases the likelihood of a successful session hijacking attack. This can be seen as a control against preventing other attacks. A session can immediately be terminated if any foul play from a user is detected.
Access Revocation
Implement secure controls by allowing security teams to grant access with limitations. If an employee or contractor has left the company, access can be terminated instantly. There is no residual access when a user is terminated or device is deactivated.


Tamper Proof Logs
Procyon audit logs enable time-sensitive tracking and visibility into users’ activities. Procyon’s use of TPM to store user identity gives audit logs the power to not be interfered with or changed – preventing hackers from hiding their trail.
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.
Risk Analysis and Mitigation Across Multi-cloud
Protect your organization’s cloud infrastructure by automating risk analysis for all permissions granted to all resources across multi-cloud.

Apply Least Privilege to All Cloud Infrastructure Access
With least privilege access, users are given the minimum level of access they need to do their job. Flexible controls close the security loopholes associated with over privilege access to enable maximum security of your cloud infrastructure.
Simplify IAM Operations
IAM operations have become complex with tedious processes to manage. Each cloud provider now has tens of thousands of permissions – often preventing users from fully utilizing the cloud. Procyon makes IAM operations easy and consumable for DevOps with simple workflows and dynamic custom roles.


Reduce Operational Costs
Simplify governance and bolster security with identity access management that allows you to give the right people access to the right resources at the right time. Remove the bottleneck of centralized IT for greater productivity and cost savings.
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.

Collect evidence for compliance across your cloud infrastructure
Procyon is SOC 2 compliant so you can rest assured that your data is safe, secure, and protected from unauthorized access.

Maintain Continuous Compliance
Build a compliance framework crosswalk that allows you to simultaneously map your controls to multiple frameworks or regulations (e.g. CIS, HIPAA, ISO, SOC 2, etc.). Compliance teams can automate the compliance process using unique user identification and access management controls.
Comprehensive Protection Through Least Privileged Access
Procyon can help you reveal, prioritize and remediate security gaps with insight and precision, accelerating action, least privilege, and security collaboration throughout your organization, eliminating any long-standing privileged accesses.


Digging Deeper into Your Audits
Procyon provides full AWS cloud observability and visibility of security and compliance so that you can get a more profound context into what is happening within your cloud environment. Get information at your fingertips: Who accessed what, when, how long, which device, and which permission.
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.
Recent Resources
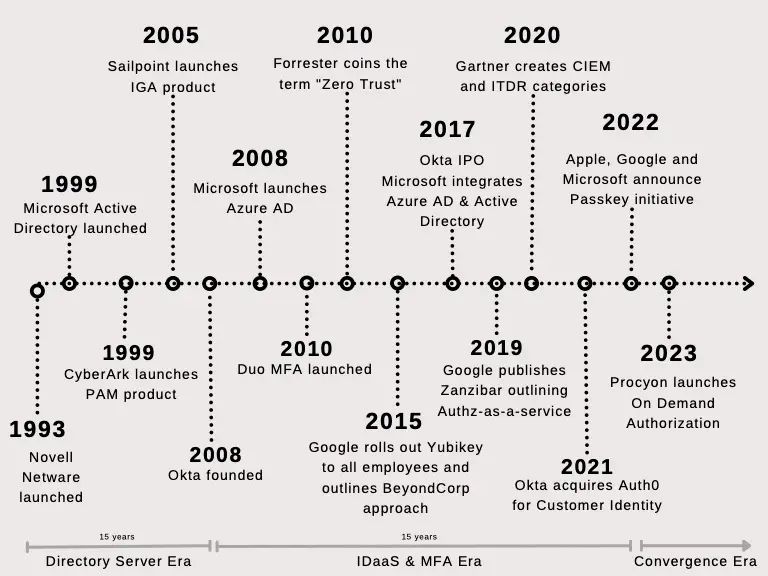
Identity and access management traces its roots back to the mainframe era. DoD first employed logical...
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology....
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now...
Get in touch
Want to know more about our product? Please fill out the form and share your message with us.
- Request a demo
- Business tiers and pricing
- General questions